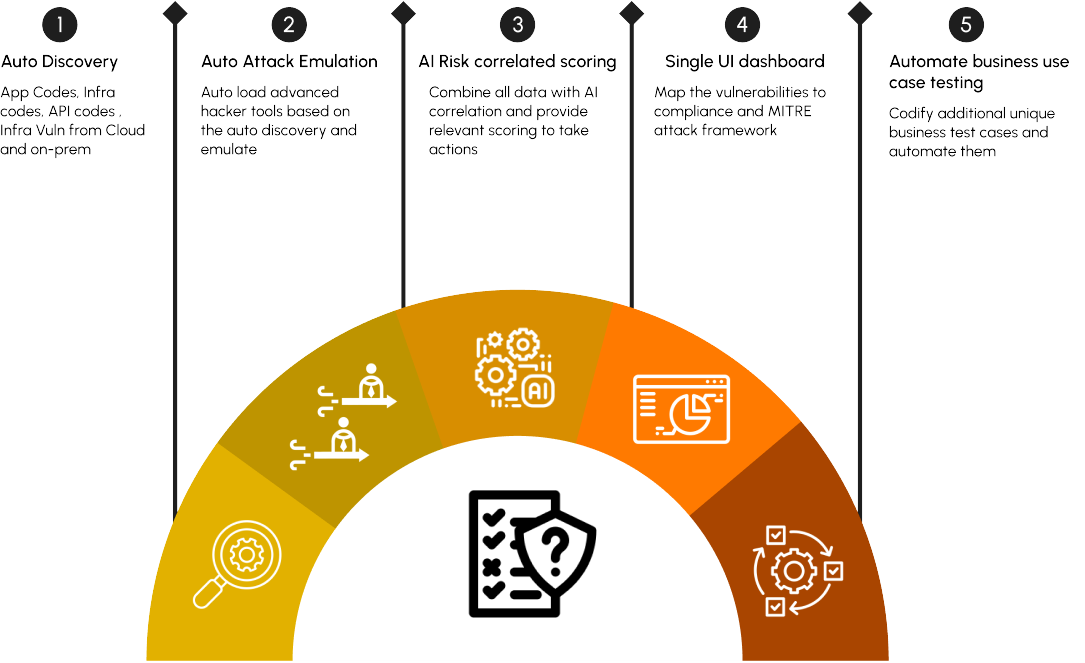
Automated Pen Testing
Providing C-suites and security teams with hacker lens visibility into advanced cyber attacks with multi layer automated penetration testing in a single dashboard
O2Cyber delivers penetration testing (pen testing) services by combining automated tools and human expertise. Following a modern approach to penetration testing and leveraging a diverse set of tools and techniques, helping organizations identify and address security vulnerabilities proactively, enhance their overall security posture, and mitigate the risk of cyber attacks and data breaches.
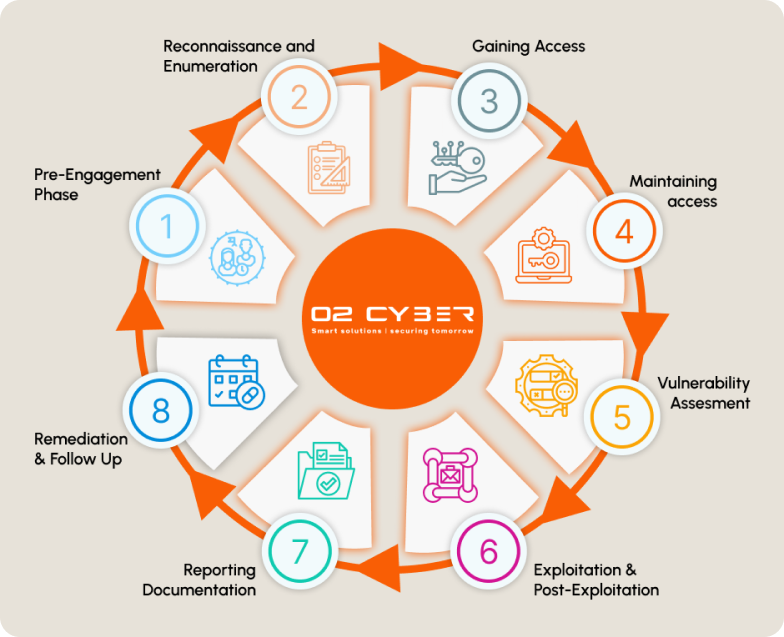
Our Approach
Pre-Engagement Phase:
- Scope Definition: Clearly define the scope, objectives, and rules of engagement for the penetration test, including the systems, networks, applications, and target assets to be assessed.
- Agreement and Authorization: Obtain written consent and authorization from the organization's stakeholders to conduct the penetration test, ensuring compliance with legal and regulatory requirements.
- Information Gathering: Gather preliminary information about the organization's infrastructure, technologies, and potential attack surfaces through passive reconnaissance techniques, such as open-source intelligence (OSINT) and network enumeration.
Reconnaissance and Enumeration:
- Active Reconnaissance: Conduct active reconnaissance to identify live hosts, network services, and system vulnerabilities using tools
- Enumeration: Enumerate network resources, user accounts, and application endpoints to gather additional information that can be leveraged in subsequent attack phases.
Gaining Access
- This stage uses web application attacks, such as cross-site scripting, SQL injection and backdoors, to uncover a target’s vulnerabilities. Testers then try and exploit these vulnerabilities, typically by escalating privileges, stealing data, intercepting traffic, etc., to understand the damage they can cause.
Maintaining access
- The goal of this stage is to see if the vulnerability can be used to achieve a persistent presence in the exploited system— long enough for a bad actor to gain in-depth access. The idea is to imitate advanced persistent threats, which often remain in a system for months in order to steal an organization’s most sensitive data.
Vulnerability Assessment:
- Automated Scanning: Use vulnerability scanning tools to perform automated scans of the target infrastructure and identify known vulnerabilities in systems, services, and applications.
- Manual Assessment: Augment automated scanning with manual vulnerability assessment techniques, including manual verification of identified vulnerabilities and validation of potential exploitability.
Exploitation and Post-Exploitation:
- Exploitation of Vulnerabilities: Attempt to exploit identified vulnerabilities to gain unauthorized access to systems, escalate privileges, and compromise sensitive data.
- Post-Exploitation Activities: Conduct post-exploitation activities, such as lateral movement, privilege escalation, and data exfiltration, to simulate the actions of a real-world attacker and assess the extent of potential damage.
Reporting and Documentation:
- Findings Documentation: Document all identified vulnerabilities, exploits, and attack paths discovered during the penetration test, including detailed descriptions, risk assessments, and remediation recommendations.
- Executive Summary: Prepare an executive summary highlighting key findings, risk exposure, and actionable recommendations for senior management and stakeholders.
- Technical Report: Provide a detailed technical report with comprehensive information about each vulnerability, including proof-of-concept (PoC) exploits, attack vectors, and remediation guidance for IT and security teams.
Remediation and Follow-Up:
- Remediation Guidance: Collaborate with the organization's IT and security teams to prioritize and remediate identified vulnerabilities based on their severity and potential impact on business operations.
- Re-Testing: Conduct follow-up penetration tests to validate the effectiveness of remediation efforts and ensure that identified vulnerabilities have been adequately addressed.
- Continuous Improvement: Provide recommendations for improving the organization's overall security posture, including the implementation of security best practices, employee training programs, and ongoing vulnerability management processes.
Our Approach
Pre-Engagement Phase:
- Establishing clear parameters defining the scope and objectives of the penetration test, alongside obtaining written consent from stakeholders, is crucial to ensure compliance with legal requirements, while also gathering preliminary information through passive reconnaissance techniques
Reconnaissance and Enumeration:
- Perform active reconnaissance to uncover live hosts, network services, and system vulnerabilities, while also enumerating network resources, user accounts, and application endpoints to collect supplementary data for subsequent attack stages.
Gaining Access
- Web application vulnerabilities such as cross-site scripting, SQL injection, and backdoors are exploited by testers to assess potential damage through actions like privilege escalation, data theft, and traffic interception.
Maintaining access
- Determine if the vulnerability permits sustained access to the compromised system, akin to advanced persistent threats, which linger within systems for extended periods to pilfer critical organizational data
Vulnerability Assessment:
- Combine automated scanning with manual assessment techniques to comprehensively identify and validate known vulnerabilities in systems, services, and applications
Exploitation and Post-Exploitation:
- Exploit identified vulnerabilities for unauthorized access, escalate privileges, and compromise sensitive data, proceed with post-exploitation activities like lateral movement and data exfiltration to mimic real-world attacker behavior and gauge potential damage
Reporting and Documentation:
- Comprehensively document all penetration test findings, including vulnerabilities and exploits and attack paths in detailed reports tailored for different stakeholders' needs
Remediation and Follow-Up:
- Engage with the organization's IT and security teams to prioritize and address vulnerabilities, conduct follow-up tests to verify remediation effectiveness, and offer suggestions for enhancing overall security through best practices, training, and ongoing vulnerability management.
