Ransomware Preparedness
Ransomware Recovery - A Layered Recovery Response
Ransomware operators are shifting from moving laterally and relying solely on encryption to other forms of cyber extortion, including nonrecoverable data corruption, hardware corruption, data theft and data mining. Additionally, ransomware-as-a-service (RaaS) models continue to proliferate, enabling less technically skilled threat actors to launch ransomware attacks with greater ease and sophistication. It's important to stay updated on emerging trends and implement robust cybersecurity measures to mitigate the risk of ransomware attacks.
"Even the most well-funded organizations cannot address all threats. Responding to the threat landscape is about prioritization. This means simultaneously prioritizing known threats and preparing for the uncertain threats."
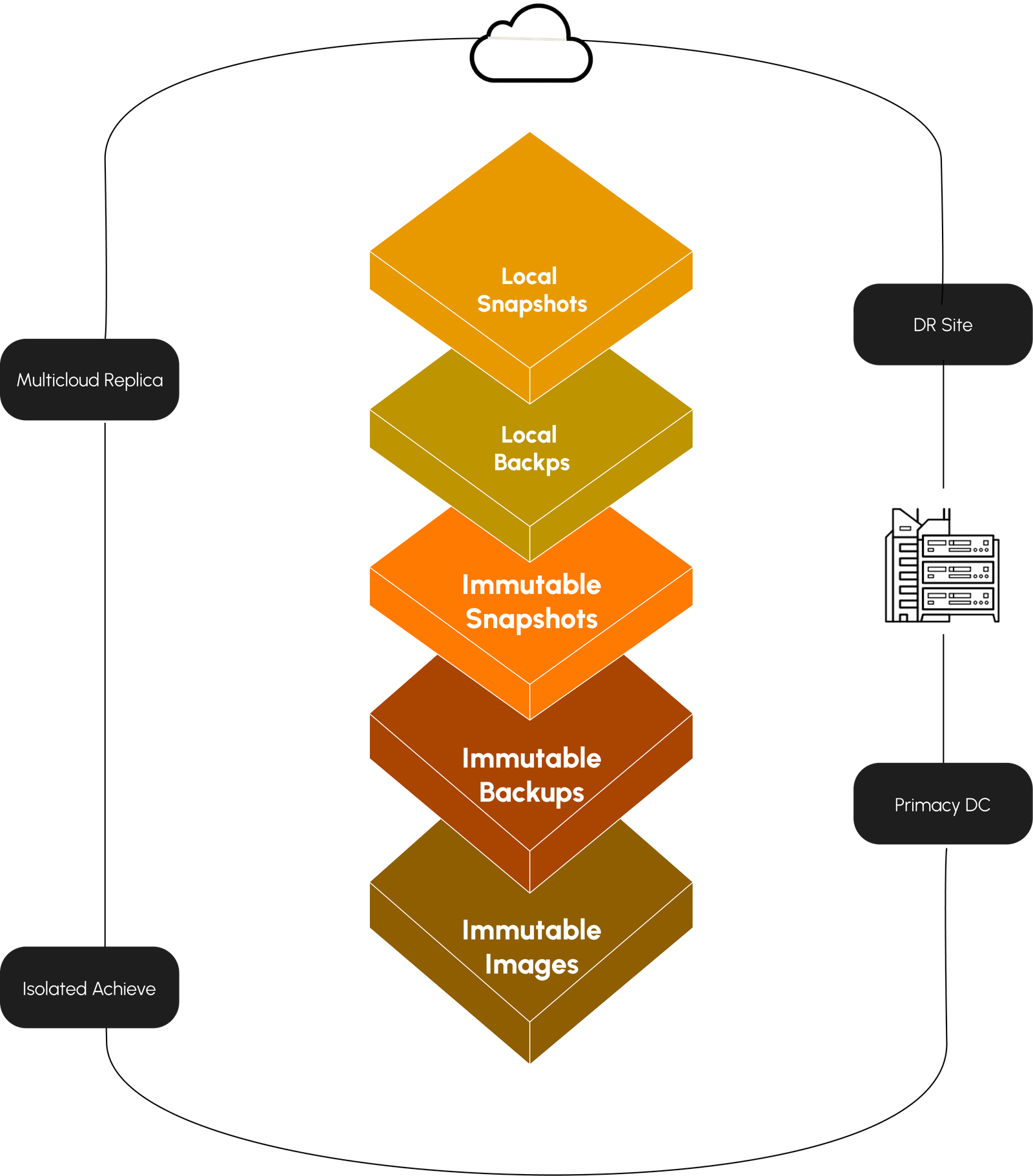
- Analysis-Effective ransomware recovery requires a layered approach to data protection
- Make recovery of directory services paramount
- Build an Architecture That Proactively Solves Business-Critical Recoverability
- Prioritize and Recover Non-Business-Critical Datasets
There are four critical elements that need to be done successfully to recover from ransomware:
- Identification of critical datasets
- Protect directory services
- Establish backup target hierarchy to optimize recovery
- Align critical datasets to fast storage media
Recommendations:
- Security and risk management leaders, including chief information security officers (CISOs), should:
- Maintain effectiveness against top threats by monitoring microtrends — the smaller changes within a threat category — and measuring drifts in security control effectiveness.
- Expand the current roadmap by planning future organizational security investments to prepare for the most likely high-momentum threats, where current posture lags behind attackers.
- Determine the impact of the risks coming from uncertain threats lacking supporting facts and that are potentially overhyped. Do this by categorizing threats based on relevance, urgency, feasibility of attacks, maturity and measurability of remediation actions.
- Account for nontechnology threats in your future modeling by incorporating potential threats originating from assets, events and behaviors that the organization has no direct control over.
Make Recovery of Directory Services Paramount
When your identity provider is impacted by ransomware, datasets and applications dependent on those accounts for permissions become inaccessible (even if they were not affected by the malware). Without a backup and the ability to recover, recreation of user accounts, service roles and federated networks would need to be done manually. Having a separate immutable and isolated backup of directory services will greatly improve response time required to provide access to the environment and begin to initiate recovery. To optimize speed of recovery, this dataset must be as close as possible to the production or the recovery environment, and best practice dictates these sets be exported to an off-premises isolated storage environment.
Build an Architecture That Proactively Solves Business-Critical Recoverability
Business-critical datasets identified within disaster recovery and business continuity plans must be adequately protected and stored in a storage target that will optimize recoverability. Critical applications such as ERP, email and CRM could be prioritized due to the impact an outage will have on operations and the business risk a prolonged outage represents. Consider the datasets that are constantly in use by the largest percentage of your user and client base, including configuration files/settings for your critical infrastructure (DNS, firewalls, routers, switches, etc.).
Prioritize and Recover Non-Business-Critical Datasets
MSEs should keep recovery tiers to an absolute minimum. In doing so, recovery of the remaining datasets will occur in the most operationally efficient manner possible, simplifying the process and restoration. These will range from user specific data to other unstructured datasets. Some examples are:
- Individual user directories
- Regulatory data hold
- Historical projects
- Archived reports, audits, etc.

