SOC
Strengthening Your Defenses: Our Comprehensive Approach to Cyber Security Operations
At O2Cyber, we understand the evolving landscape of cyber threats and the critical importance of robust security operations to safeguard your organization's assets and data. Our comprehensive approach to Cyber Security Operations is designed to provide proactive threat detection, rapid incident response, and continuous improvement to help our clients mitigate risks and stay ahead of cyber adversaries.
"Next generation SOC should be driven by predictive threat intelligence , incidents detected based on adaptive kill chain, remediation built on well defined automated workflow process and equipped with a well practiced CSIRP process" -O2 Cyber SOC team
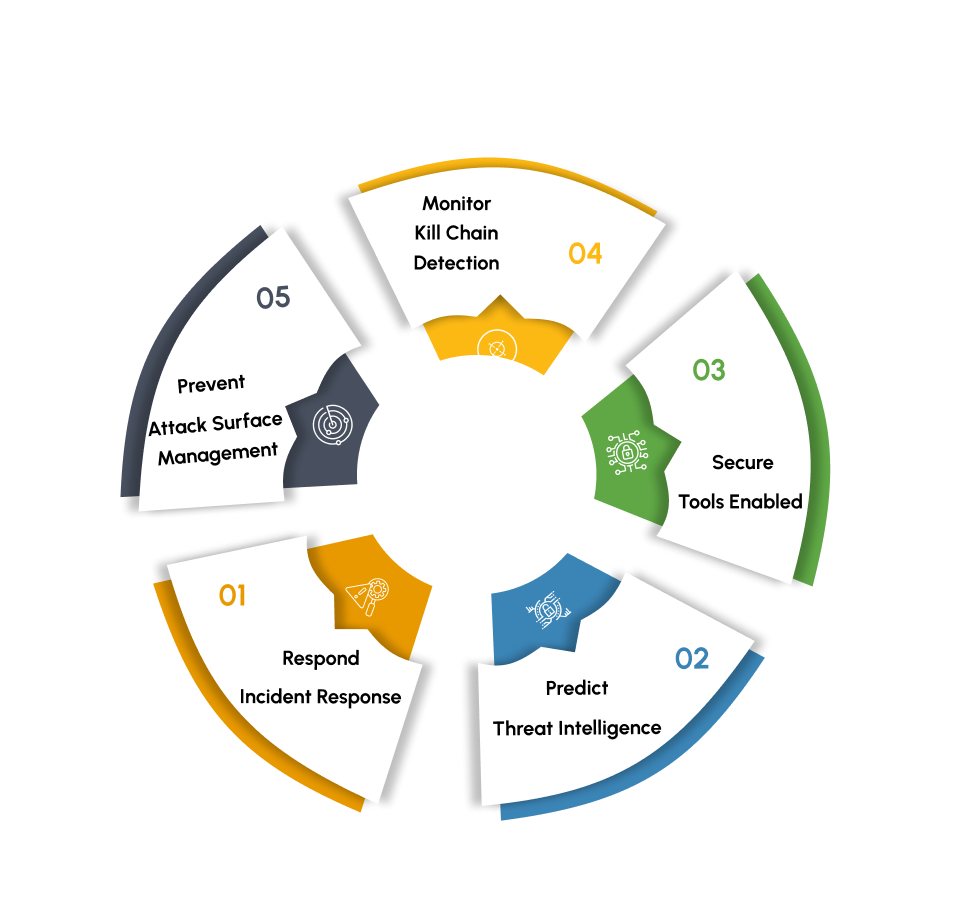
Our approach
Security Operations goal is to create an ability to analyze risk proactively which will reduce threat exposure and improve detection capabilities using advanced technology and fine tuned processes. SOC should be built to respond to the incidents that will impact the brand value and operations of the organization in a catastrophic manner.

Comprehensive Monitoring and Analysis
Our Cyber Security Operations Center (CSOC) operates 24/7, utilizing advanced Behavioral Analytics SIEM technology to monitor your systems, networks, and endpoints for any signs of suspicious activity. Our team of skilled analysts is trained to analyze vast amounts of data from multiple sources, including network logs, IAM logs, and DNS/domain logs, to detect potential threats and security incidents in real-time.
Early Threat Detection and Response
With our Early Threat Detection and Response (EDR) capabilities, we are able to identify and respond to threats before they escalate. By correlating data from various sources and leveraging behavioral analytics, we can detect anomalies and potential indicators of compromise, allowing us to take immediate action to mitigate the threat and minimize the impact on your organization.


Proactive Threat Intelligence Integration
Our approach to Cyber Security Operations is enriched by the integration of threat intelligence feeds from reputable sources. By staying abreast of the latest threat intelligence, including emerging threats, attack vectors, and malicious actors, we can better anticipate and defend against evolving cyber threats.
Incident Management and Response
In the event of a security incident, our team is equipped to respond swiftly and effectively. We follow a structured incident management process, which includes containment, eradication, and recovery procedures, to minimize the impact on your business operations and restore normalcy as quickly as possible.


Continuous Improvement and Optimization
Our commitment to excellence extends beyond incident response. We believe in continuous improvement and optimization of our Cyber Security Operations. Through regular assessments, reviews, and feedback mechanisms, we strive to enhance our processes, technologies, and expertise to better serve your evolving security needs.
People operational model
Similar to incident review levels, our typical SOCs adopt a hierarchical approach. In this hierarchy, analysts and engineers are categorized based on their skill set and experience. A typical team might be structured into four levels with new advancements in technology, we are adopting the next generation approach, for example.
Level 1: First responders
The first line of incident responders are group of security analysts who will be eyes on glass 24x7 and watch for alerts.
Level 2: Cyber Incident remediation
These personnel can quickly get to the root of the problem and assess which part of your infrastructure is an issue.
Level 3: Proactive security operations
The security managers are informed and specialist crew are involved and begin moving from reactive to proactive security actions.
Level 4: Cyber Security Incident Response Process
At the SOC’s most advanced level are managers and chief officers and they will be more engaged and execute this process.
Why O2Cyber:
- Built advanced 24x7 SOC fusion centers across the globe with the best in response time
- Implemented continuous threat exposure management (CTEM) concepts to a dynamically growing threat landscape
- Automated security dashboard with advanced AI based correlation exposing vulnerabilities in an actionable way
- Creation of advanced playbooks and orchestration with escalation path protocol
- Applying a business-relevant approach to improve the breadth and relevance of detection and response.
- Predictive threat intel driven Cyber SOC for next generation defense
- Leveraging generative cybersecurity AI for operational efficiency gains and skill augmentation
