Data Protection and Privacy
Business Is the foundation for Data Security
Data is the cornerstone of digital business and includes a wide spectrum of sourced and derived data. It can include information needed by service employees, partners and customers. This data may be sensitive, such as Intellectual property (IP), Trademarks, personally identifiable information (PII), personal health information (PHI), payment card information (PCI) or other regulated data, internal and external communications. It may also include other sensitive or confidential information, and the continually growing use cases for data and analytics, including widespread adoption of AI.
"Enhance data classification initiatives through the implementation of policies, processes, and tools that extend beyond mere classification, recognizing data security as a distinct domain, and leveraging automation for efficiency."
O2 Cyber approach
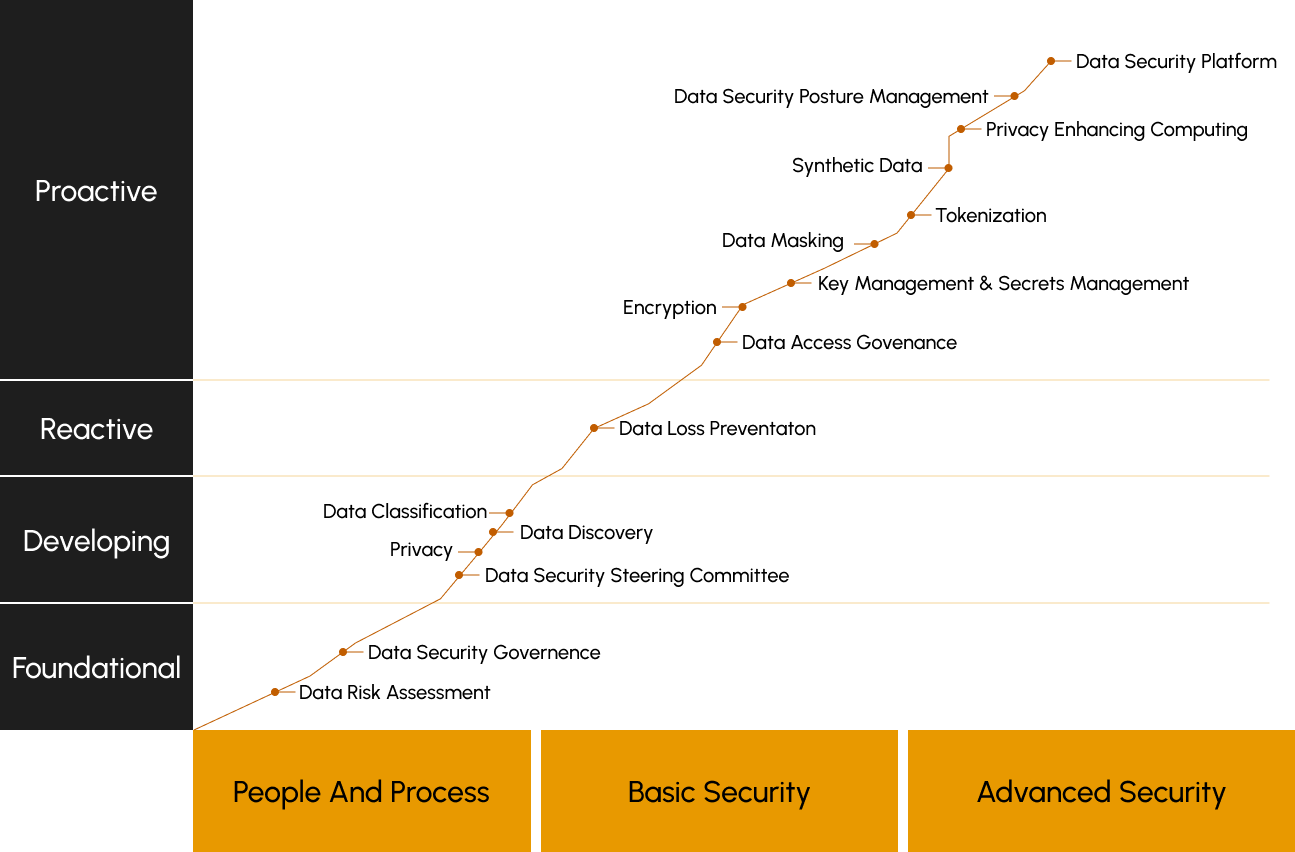
The modern approach to providing data security involves a multi-faceted strategy that addresses the complex challenges of protecting sensitive information in today's dynamic threat landscape. Here are key elements of a modern data security approach:
Data Classification and Inventory:
- Data Identification: Identify and classify sensitive data based on its type, sensitivity, and regulatory requirements.
- Data Inventory: Maintain an inventory of all data assets, including their location, ownership, and access controls.


Risk Assessment and Compliance:
- Risk Analysis: Conduct regular risk assessments to identify potential threats, vulnerabilities, and risks to data security.
- Compliance Frameworks: Align data security practices with relevant regulatory requirements and industry standards (e.g., GDPR, HIPAA, PCI DSS).
Data Encryption and Tokenization:
- Data Encryption: Encrypt sensitive data at rest, in transit, and during processing using strong encryption algorithms and key management practices.
- Tokenization: Replace sensitive data with randomly generated tokens to reduce the risk of exposure in storage and transmission.


Data Loss Prevention (DLP):
- Endpoint Protection Platforms (EPP): Deploy EPP solutions to protect endpoints from malware, ransomware, and other advanced threats.
- Data Encryption: Encrypt data stored on endpoints, laptops, and mobile devices to prevent unauthorized access in case of loss or theft.
Employee Training and Awareness:
- Security Awareness Training: Provide regular training and awareness programs to educate employees about data security best practices, social engineering attacks, and phishing threats.

