Managed Services
Unlock Your Team’s Full Potential with Our Expert Managed Services
As a cybersecurity technology consulting firm, our approach is structured and comprehensive, ensuring that our clients receive tailored solutions to their unique challenges and needs. Here's how we guide our clients through the process:
Growing significance of Managed security services:
Managed security has emerged as a practical approach for understaffed security teams to rapidly build, maintain, and scale a strong cybersecurity function in a fast-paced and ever-evolving landscape. Organizations increasingly rely on MSS offerings to support some, or all, of their cybersecurity needs because of the following:
Growing threat landscape
Increasing number of adversaries
Remote working
Skills shortage
Cost of Data breaches
Security Services Capability
We provide an end to end security services with comprehensive planning that is customized based on the risk assessment. Business outcomes are prioritized and mapped to a step by step strategy to achieve the outcomes as part of 1-3 year plan. Our range services includes the following areas,
Security Services Capability
We provide an end to end security services with comprehensive planning that is customized based on the risk assessment. Business outcomes are prioritized and mapped to a step by step strategy to achieve the outcomes as part of 1-3 year plan. Our range services includes the following areas,

Risk Assessment and Gap Analysis
Lorem ipsum dolor sit amet, consectetur adipiscing elit.

Security Strategy
Lorem ipsum dolor sit amet, consectetur adipiscing elit.

24x7 SOC
Lorem ipsum dolor sit amet, consectetur adipiscing elit.

Vulnerability Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit.

Penetration Testing
Lorem ipsum dolor sit amet, consectetur adipiscing elit.
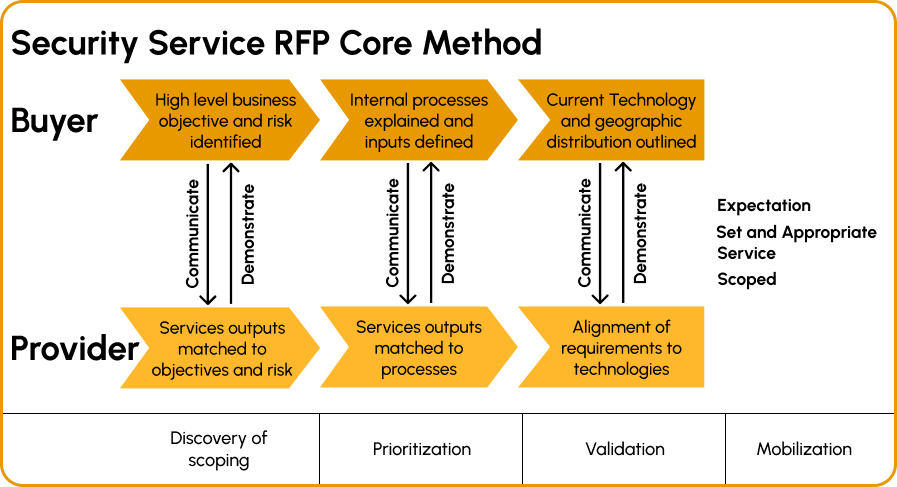
MSSP Onboarding
Our Managed Security Services Provider (MSSP) onboarding process starts with an in-depth consultation to understand your organization's security needs, challenges, and objectives. This allows us to tailor our services to your specific requirements.
Benefits of partnering with O2Cyber
24/7 Monitoring and Response with SOC:
We offer around-the-clock monitoring and real-time threat detection capabilities, providing organizations with continuous protection against cyber threats and minimizing the risk of security breaches.
Cost-Effectiveness:
Our model can be more cost-effective than hiring and maintaining an in-house security team. We typically offer flexible pricing models that allow organizations to pay for only the services they need.
Access to Advanced Technologies:
We invest in state-of-the-art security technologies and tools, which may be cost-prohibitive for many organizations to implement on their own. By partnering with us, organizations gain access to these advanced technologies without the need for significant upfront investments.
Faster Incident Response and Recovery:
We have established incident response processes using proven playbooks and procedures in place to quickly identify, contain, and mitigate security incidents. This rapid response capability minimizes the potential impact of security breaches and helps organizations recover more quickly from cyber attacks.
Focus on Core Business Activities:
By outsourcing security responsibilities to us, organizations can free up internal resources and focus on core business activities. This allows employees to concentrate on strategic initiatives and revenue-generating projects without being bogged down by security-related tasks.
Benefits of partnering with O2Cyber
24/7 Monitoring and Response with SOC:
24/7 Monitoring and Response with SOC:
We offer around-the-clock monitoring and real-time threat detection capabilities, providing organizations with continuous protection against cyber threats and minimizing the risk of security breaches.
Cost-Effectiveness:
Cost-Effectiveness:
Our model can be more cost-effective than hiring and maintaining an in-house security team. We typically offer flexible pricing models that allow organizations to pay for only the services they need.
Access to Advanced Technologies:
Access to Advanced Technologies:
We invest in state-of-the-art security technologies and tools, which may be cost-prohibitive for many organizations to implement on their own. By partnering with us, organizations gain access to these advanced technologies without the need for significant upfront investments.
Faster Incident Response and Recovery:
Faster Incident Response and Recovery:
We have established incident response processes using proven playbooks and procedures in place to quickly identify, contain, and mitigate security incidents. This rapid response capability minimizes the potential impact of security breaches and helps organizations recover more quickly from cyber attacks.
Focus on Core Business Activities:
Focus on Core Business Activities:
By outsourcing security responsibilities to us, organizations can free up internal resources and focus on core business activities. This allows employees to concentrate on strategic initiatives and revenue-generating projects without being bogged down by security-related tasks.





