Security Strategy for the Age of AI

A cybersecurity strategy offers a clear, detailed plan that standardizes security across an organization. It helps CISOs shift from reactive to proactive security, ensuring that they are ready and prepared to respond to various relevant advanced persistent threats . CISOs should approach AI with a strategic mindset, ensuring its ethical use, robust security measures, and integration into existing cybersecurity frameworks to enhance threat detection, response capabilities, and overall resilience against evolving cyber threats.
"CISO for modern times should be resilient , threat aware , an excellent communicator, provide visionary leadership to people and develop a predictive threat intelligence driven proactive cyber practice tracked with metrics "
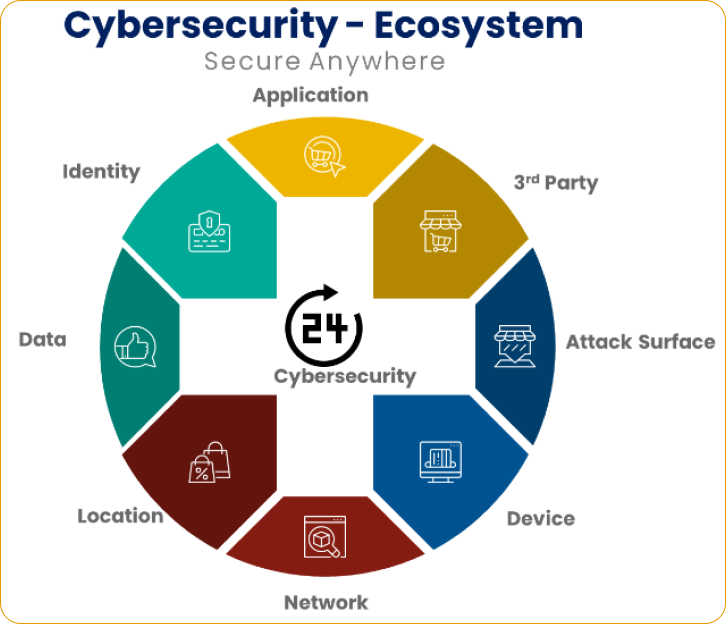
CISO Strategy and Roadmap - Phases and goals
Effective chief information security officers (CISOs) primarily excel as leaders, managers, and communicators, rather than being solely focused on technical expertise. . The success of a CISO hinges on accomplishing two critical objectives: first, building a personal brand characterized by credibility and leadership, and second, establishing the groundwork for a security program that is resilient and defensible. We approach it in 4 big phases which encompasses the following:
ASSESS
- Assess the type of CISO that your enterprise requires Operational driven Vs Business driven
- Understand your enterprise’s structure: organization charts and operational documents
- Identify key stakeholders: Create a list of leadership stakeholders with whom you’ll be working. This list may include (but is not limited to) the CEO, CFO, CIO, general counsel, head of HR, chief privacy officer (CPO) and chief risk officer (CRO )
- 7 Point stakeholder and staff discussion questionnaire
- Actions in assess phase includes inventory and assessments of Physical security, Business continuity and disaster recovery (BC/DR), Data protection and Privacy, Compliance, IT risk , Risk governance, Security operations , attack surface reduction, Audit findings, Vulnerability assessments, Threat assessments, Talent assessments, Regulatory findings, Penetration tests , Phishing tests
PLAN
- The key for this phase is a documented strategic plan that prioritizes security initiatives for your first year, and a roadmap for your 3 year program. An operational budget that ensures sufficient resources to achieve priorities. If resources are lacking, then the strategic plan should be adjusted accordingly so it is achievable.
- Create a well defined security strategy that layout the strategic and tactical vision with roadmap for people, process and technology functions
- Select few top priorities in discussion with leadership teams
- Organize your security functions
- Plan your operational and capital budget
- Communicate effectively to everyone in the organization. Run a road show campaigns about the cyber security program vision

As part of planning the key item is Strategy. It should include shift left operating model and it should be forward looking and driven by intelligence and would focus on shift left model. The program should be built to be spend more time on the left rather than on the right side which is a fire drill.

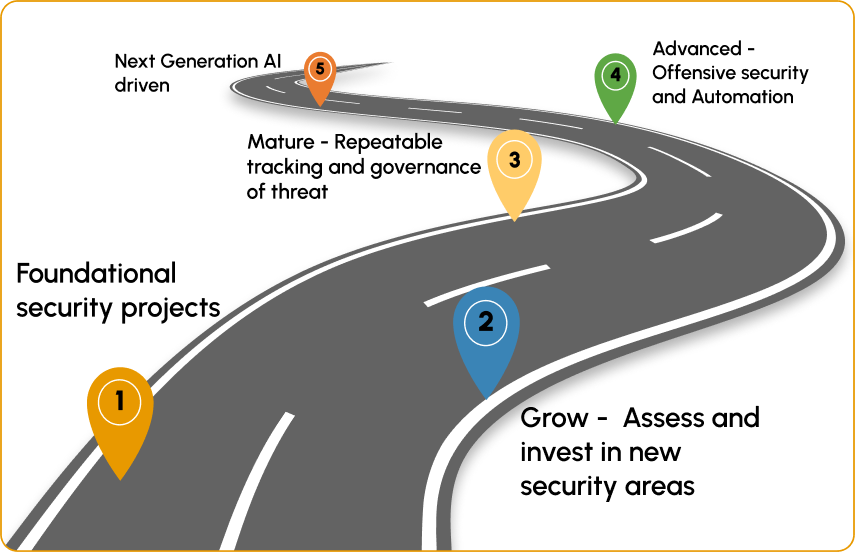
ACT
Define roles, functions and responsibilities: All manager level roles and have a clear understanding of their role and accountable for and how they are assessed.
Project ownership:
Each of your strategic priorities should have a formal project owner. Establish a clear plan, expectations and outcomes for each project, and clarify these with respective project owners
Leadership buy-in:
Use your strategic plan and security vision to engage leadership and get buy-in for your top priorities.
Security governance:
Begin work to build effective information risk governance across the enterprise. This entails risk decision-making rights, risk accountability and the responsibilities of stakeholders across the enterprise for information risk
Socialize your strategic plan and vision:
Present your strategic plan and vision to leadership and stakeholders across the enterprise
Meetings:
Schedule team meetings for check-ins to plan and track with your lead team, monthly security staff meetings, all hands meeting for major announcements and stand in meetings for facilitating collaboration
REPORT:
The report phase provides evidence of your impact on security and the enterprise. Measurement and communication are hallmarks of a successful CISO, and you should dedicate significant effort to this endeavor throughout your tenure.
Define metrics: Define a portfolio of security metrics: Create a small portfolio of operational KPIs and then adapt these operational metrics into business-relevant metrics that resonate with leadership and the board.
Develop an executive reporting process: Establish reporting frequency and audiences, such as the steering committees, C-suite briefings and board reporting (full board and risk committee). Once reporting expectations are set, spend time understanding the expectations and priorities of each audience.
Monitor program and project progress: Track security’s progress and program maturity gains. Report progress to leadership, and use this momentum to make the business case for continued (or increased) funding and support as needed.
Highlight early wins and challenges: Maintain momentum by communicating wins and identifying solutions to address challenges as they emerge CISO Dashboard : Build a dashboard to showcase the efficient of the program plus high priority risks. It serves as a great tracker in one place.
Where strategy meets the world AI transformation - The power of strategy
Your success is our priority, and we believe that achieving it should never be a compromise between automation and human touch. With O2 Cyber, you get the best of both worlds, ensuring that every decision you make is guided by efficiency and expertise. Say goodbye to inefficient manual processes as we lead the way to a future where you can save time and resources, with the acceleration of automated processes.

