Threat Intelligence and Hunting
Predictive threat Intel driven next gen cybersecurity operations - Right Intel for Right Job
Our next generation security operations teams identify real-time threats and assist in predicting not just which future threats may impact your business but also explain how by blending in Cyberthreat Intelligence (CTI) as a key capability for any SecOps function. In the world of cybersecurity, advanced persistent threats (APTs) and defenders are constantly trying to outmaneuver each other. Data on a threat actor’s next move is crucial to proactively tailoring your defenses and preempt future attacks.
"Currently, no single source of threat intelligence, whether open-source, commercially available, or government-developed, provides comprehensive visibility into all aspects of the market. "
TI program Challenges at Organizations
Unqualified TI sources
SOCs often report threat intelligence ineffectively to stakeholders, missing opportunities to increase risk awareness and demonstrate the value of the capability.
TI Siloed
Organizations lack integration in their approach to threat intelligence, primarily contained within the security operations center (SOC), leading to isolated prioritization of requirements.
Lack of strategic oversight
Security and risk management (SRM) leaders struggle to establish mature threat intelligence capabilities, facing challenges in collecting appropriate intelligence, resource allocation, and strategic oversight.
TI Foundations not established
Defining defensible threat intelligence budgets remains a challenge for SRM leaders due to overlooked foundational principles, hindering long-term objective achievement.
Effective TI program should enable
- Sheds light on the unknown, enabling security teams to make better decisions
- Empowers cyber security stakeholders by revealing adversarial motives and their tactics, techniques, and procedures (TTPs)
- Ensure that data classification processes and tools take account of the full life cycle of data, and that controls remain effective and appropriate when classification changes.
- Start with focused initiatives that address funded business needs, such as regulatory compliance, and that have well-defined project scopes.
Components of Threat Intelligence Function

People
- Team Structure
- Roles and Responsibilities
- Strategic Oversight

Process
- Collection
- Use Cases Analysis & Distribution
- Applying Predictive & Defensive Courses Of Action
- All Reporting And Analysis

Integration Into Business Units
- SOC
- Risk Management
- Business Engagement

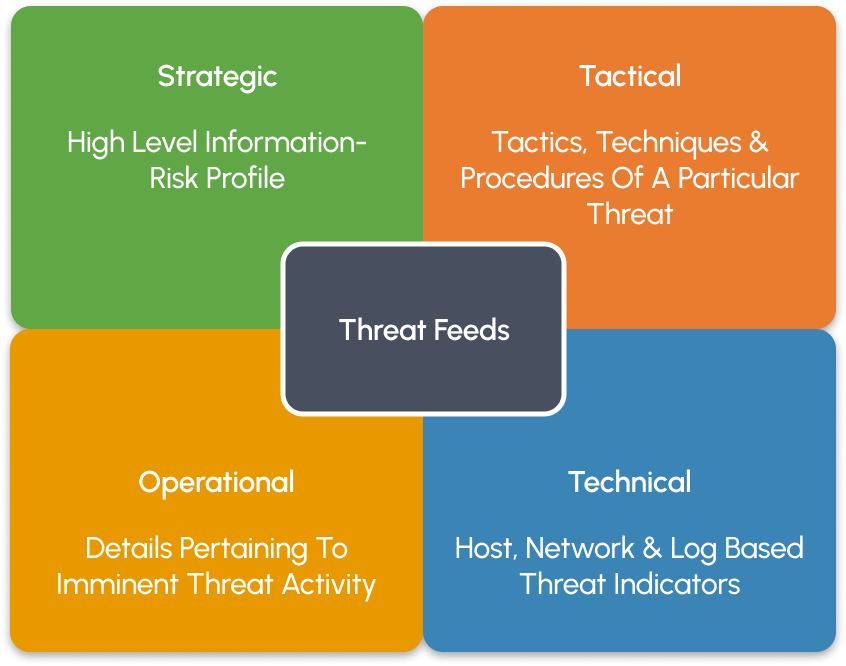
Threat Intelligence Feeds
- Strategic
- technical
- Tactical
- Operational

Threat Intelligence Feeds
- Strategic
- technical
- Tactical
- Operational
Threat Intelligence feeds
Identify and add capabilities to expand offering to various personas. Develop a strategy to feed business centric users rather than just technical users. When thinking about your organization overall, it’s highly encouraged to reach leaders beyond those who would typically come to mind for CTI enrollment (e.g., HR, Legal, Marketing, Communications, Emergency Management, Finance, R&D) and business departments that are already plugged into the SecOps ecosystem.
- At o2cyber we help product leaders take the below steps in order to leverage the impact of emerging technologies and trends on products and services,
- TO KNOW MORE --> Talk to us
